Using Identity Server and Bearer Tokens to Authenticate Sitecore
In Sitecore 9.1, Sitecore switched the authentication system from ASP.NET Membership to Identity Server 4 with ASP.NET Identity. This allows Sitecore to stop using hand-rolled bearer tokens and start using real industry standardized authentication.

In Sitecore 9.1, Sitecore switched the authentication system from ASP.NET Membership to Identity Server 4 with ASP.NET Identity. This allows Sitecore to stop using hand-rolled bearer tokens and start using real industry standardized authentication.
The switch is almost seamless for Sitecore users. They see the same Sitecore login screen and the same roles/permissions from Sitecore. What it does allow that Sitecore via OAuth can now be your main authentication system for SSO across your site infrastructure. It also allows for Sitecore to decouple the core database from the CD server, since now the ASP.NET Identity server can be anywhere. The core DB by default, you can use the link "Scripts for Sitecore Security database" found on this download page to move the security database to another DB.
NOTE: The IS4 for Sitecore has been changed via a plugin using Sitecore Host. See George Chang's blog post for a breakdown on that. And in that, they have altered it to help themselves and may have taken away some things that we need outside of Sitecore. Things like the consent page. They kind of forgot that :) But as we work on it, it will come back to what we all need.
So now that IS4 is in, what does it give us? A major benefit is it gives us a real OAuth server that we can use to authorize access to our APIs, without having to issue static tokens or logins. With this, we are able to send short-lived bearer tokens over the wire and Sitecore will authenticate those against he IS4 server.
There are two things that are REALLY important to know:
- The identity server implemented for Commerce Server is NOT the same as the one for Sitecore XP/XM. Commerce uses a custom client profile called postman-api to create the tokens and these will not work with Sitecore. They only work against the commerce APIs.
- The Sitecore Item API is still using the hand-rolled bearer tokens described here. I know it's weird; you did all the work, but left the Item API out. I would guess we will get access in a future patch to 9.1.
You can find the APIs I used here, in a sharable Postman set of API calls. Open this link and Postman will import them so you can see the APIs, and change urls/logins to suit your needs. https://www.getpostman.com/collections/a98dc7091c404c879b77
Here is the basic, super simple controller that returns json data. The important part is the [Authorize] attribute. This forces the controller through whatever security is registered with MVC.
public class MembershipController : Controller
{
[HttpGet]
[Authorize]
public ActionResult Test()
{
var test = new {TestError = "this thing"};
return Json(test, JsonRequestBehavior.AllowGet);
}
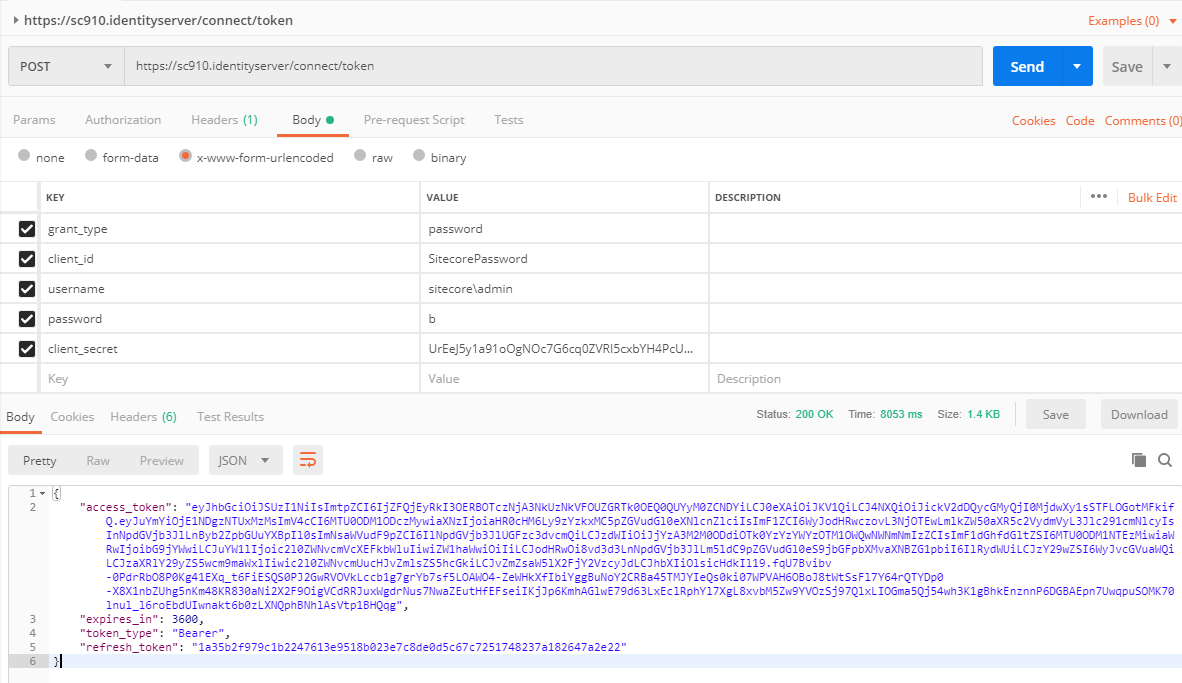
}In the image below, this is how you make a call to the identity server (https://sc910.identityserver/connect/token) to get the bearer token from the Sitecore identity server. You can find the client secret in the file \Config\production\Sitecore.IdentityServer.Host.xml in the root of the identity server.
The key to making this work is that the grant_type is password and client_id is SitecorePassword. When executing the POST request you will get an access_token back.
Notice that the request parameters are in the body and urlencoded. They are:
- grant_type
- client_id
- username
- password
- client_secret
When you make the call and it is accepted by the Identity Server, the server will return an access_token. The access_token is the bearer token. You can also see how long until it expires.
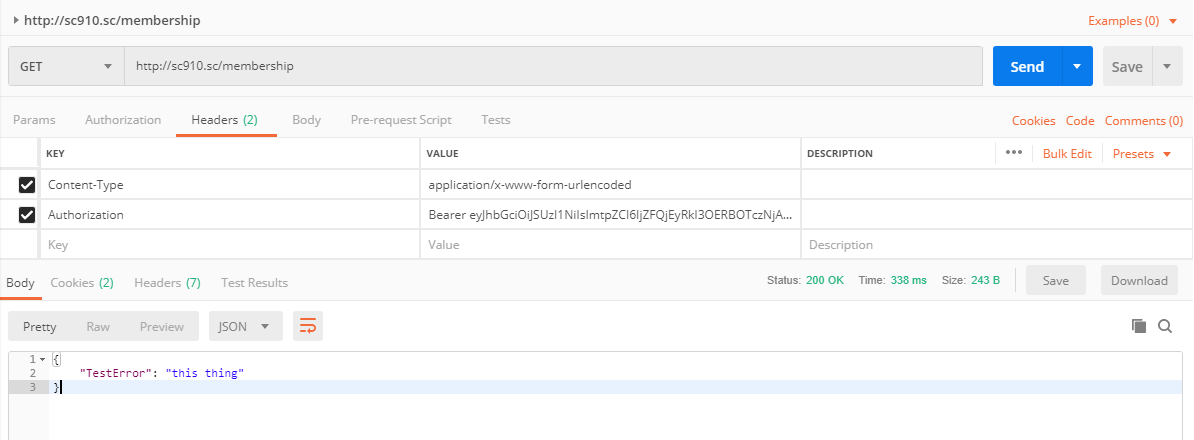
Then we can call our api passing in the bearer token, in the header as the variable Authorization. You must add the word Bearer before your token. When executed, Sitecore will authenticate your token and give you access to your API that you have designated with the [Authorize] attribute.
Notice that the request parameters are in the header. They are:
- Content-Type: application/x-www-form-urlencoded
- Authorization: You must include the word Bearer, a space and then your access_token.
This is the first step in a long road to using Sitecore as a first class OAuth server. So much more to learn.